Read autocomplete kibana.yml for more information.
The Kibana server reads properties from the kibana.yml file on startup. The location of this file differs depending on how you installed Kibana. For example, if you installed Kibana from an archive distribution (.tar.gz or .zip), by default it is in $KIBANA_HOME/config. By default, with package distributions (Debian or RPM), it is in /etc/kibana.
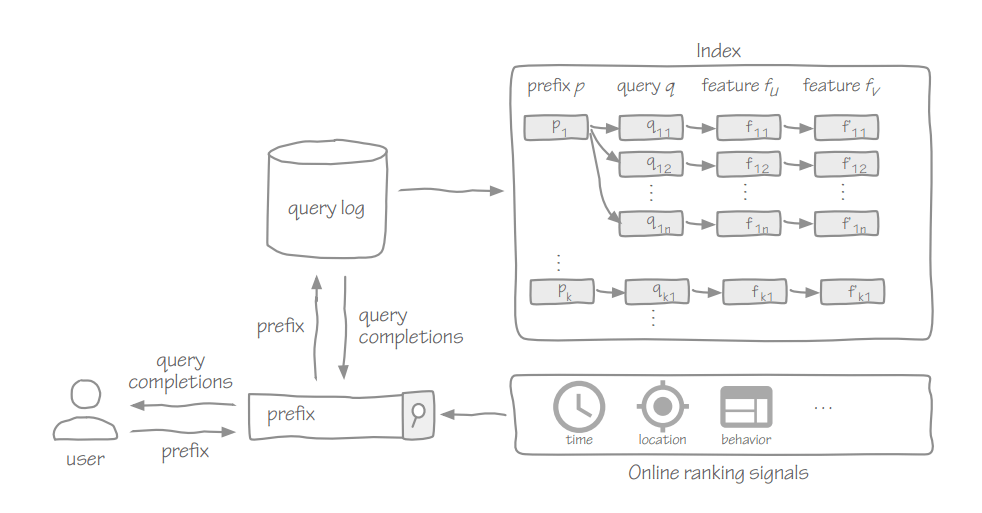
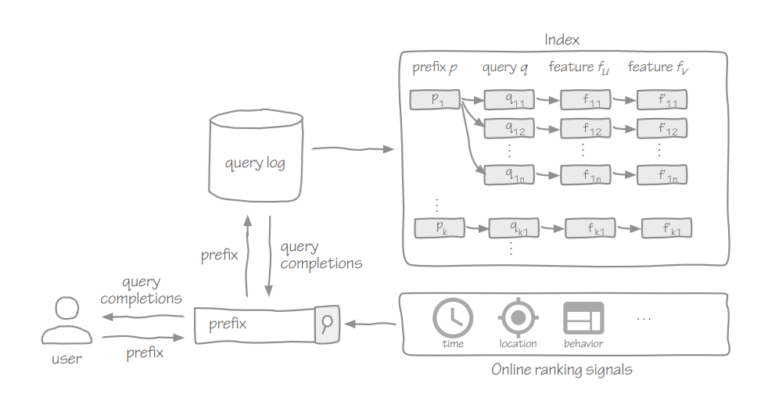
The default settings configure Kibana to run on localhost:5601. To change the host or port number, or connect to Elasticsearch running on a different machine, you’ll need to update your kibana.yml file. You can also enable SSL and set a variety of other options. Finally, environment variables can be injected into configuration using ${MY_ENV_VAR} syntax.
Add a search engine to your website at 9 USD per month
Kibana configuration settings
console.enabled:- Default: true Set to false to disable Console. Toggling this will cause the server to regenerate assets on the next startup, which may cause a delay before pages start being served.
cpu.cgroup.path.override:- Override for cgroup CPU path when mounted in a manner that is inconsistent with
/proc/self/cgroup cpuacct.cgroup.path.override:- Override for cgroup cpuacct path when mounted in a manner that is inconsistent with
/proc/self/cgroup csp.rules:- A template content-security-policy that disables certain unnecessary and potentially insecure capabilities in the browser. We strongly recommend that you keep the default CSP rules that ship with Kibana.
csp.strict:- Default:
falseBlocks access to Kibana to any browser that does not enforce even rudimentary CSP rules. In practice, this will disable support for older, less safe browsers like Internet Explorer. csp.warnLegacyBrowsers:- Default:
trueShows a warning message after loading Kibana to any browser that does not enforce even rudimentary CSP rules, though Kibana is still accessible. This configuration is effectively ignored whencsp.strictis enabled. elasticsearch.customHeaders:- Default:
{}Header names and values to send to Elasticsearch. Any custom headers cannot be overwritten by client-side headers, regardless of theelasticsearch.requestHeadersWhitelistconfiguration. elasticsearch.hosts:- Default: “http://localhost:9200” The URLs of the Elasticsearch instances to use for all your queries. All nodes listed here must be on the same cluster.
elasticsearch.logQueries:- Default:
falseLogs queries sent to Elasticsearch. Requireslogging.verboseset totrue. This is useful for seeing the query DSL generated by applications that currently do not have an inspector, for example, Timelion and Monitoring. elasticsearch.pingTimeout:- Default: the value of the
elasticsearch.requestTimeoutsetting Time in milliseconds to wait for Elasticsearch to respond to pings. elasticsearch.preserveHost:- Default: true When this setting’s value is true, Kibana uses the hostname specified in the
server.hostsetting. When the value of this setting isfalse, Kibana uses the hostname of the host that connects to this Kibana instance. elasticsearch.requestHeadersWhitelist:- Default:
[ 'authorization' ]List of Kibana client-side headers to send to Elasticsearch. To send no client-side headers, set this value to [] (an empty list). elasticsearch.requestTimeout:- Default: 30000 Time in milliseconds to wait for responses from the back end or Elasticsearch. This value must be a positive integer.
elasticsearch.shardTimeout:- Default: 30000 Time in milliseconds for Elasticsearch to wait for responses from shards. Set to 0 to disable.
elasticsearch.sniffInterval:- Default: false Time in milliseconds between requests to check Elasticsearch for an updated list of nodes.
elasticsearch.sniffOnConnectionFault:- Default: false Update the list of Elasticsearch nodes immediately following a connection fault.
elasticsearch.sniffOnStart:- Default: false Attempt to find other Elasticsearch nodes on startup.
elasticsearch.ssl.alwaysPresentCertificate:- Default: false Controls whether to always present the certificate specified by
elasticsearch.ssl.certificatewhen requested. This applies to all requests to Elasticsearch, including requests that are proxied for end-users. Setting this totruewhen Elasticsearch is using certificates to authenticate users can lead to proxied requests for end-users being executed as the identity tied to the configured certificate. elasticsearch.ssl.certificate:andelasticsearch.ssl.key:- Optional settings that provide the paths to the PEM-format SSL certificate and key files. These files are used to verify the identity of Kibana to Elasticsearch and are required when
xpack.ssl.verification_modein Elasticsearch is set to eithercertificateorfull. elasticsearch.ssl.certificateAuthorities:- Optional setting enables you to specify a list of paths to the PEM file for the certificate authority for your Elasticsearch instance.
elasticsearch.ssl.keyPassphrase:- The passphrase will be used to decrypt the private key. This value is optional as the key may not be encrypted.
elasticsearch.ssl.verificationMode:- Default: full Controls the verification of certificates presented by Elasticsearch. Valid values are
none,certificate, andfull.fullperforms hostname verification, andcertificatedoes not. elasticsearch.startupTimeout:- Default: 5000 Time in milliseconds to wait for Elasticsearch at Kibana startup before retrying.
elasticsearch.username:andelasticsearch.password:- If your Elasticsearch is protected with basic authentication, these settings provide the username and password that the Kibana server uses to perform maintenance on the Kibana index at startup. Your Kibana users still need to authenticate with Elasticsearch, which is proxied through the Kibana server.
interpreter.enableInVisualize- Default: true Enables use of interpreter in Visualize.
kibana.defaultAppId:- Default: “home” The default application to load.
kibana.index:- Default: “.kibana” Kibana uses an index in Elasticsearch to store saved searches, visualizations, and dashboards. Kibana creates a new index if the index doesn’t already exist. If you configure a custom index, the name must be lowercase and conform to Elasticsearch index name limitations.
kibana.autocompleteTimeout:- Default: “1000” Time in milliseconds to wait for autocomplete suggestions from Elasticsearch. This value must be a whole number greater than zero.
kibana.autocompleteTerminateAfter:- Default: “100000” Maximum number of documents loaded by each shard to generate autocomplete suggestions. This value must be a whole number greater than zero.
logging.dest:- Default:
stdoutEnables you to specify a file where Kibana stores log output. logging.json:- Default: false Logs output as JSON. When set to
true, the logs will be formatted as JSON strings that include a timestamp, log level, context, message text and any other metadata that may be associated with the log message itself. Iflogging.dest.stdoutis set and there is no interactive terminal (“TTY”), this setting will default totrue. logging.quiet:- Default: false Set the value of this setting to
trueto suppress all logging output other than error messages. logging.silent:- Default: false Set the value of this setting to
trueto suppress all logging output. logging.timezone- Default: UTC Set to the canonical timezone id (for example,
America/Los_Angeles) to log events using that timezone. logging.verbose:- Default: false Set the value of this setting to
trueto log all events, including system usage information and all requests. Supported on Elastic Cloud Enterprise. map.includeElasticMapsService:- Default: true Set to false to disable connections to Elastic Maps Service. When
includeElasticMapsServiceis turned off, only the vector layers configured bymap.regionmapand the tile layer configured bymap.tilemap.urlwill be available in the Maps application, Coordinate map visualizations, and Region map visualizations. map.proxyElasticMapsServiceInMaps:- Default: false Set to true to proxy all Maps application Elastic Maps Service requests through the Kibana server. This setting does not impact Coordinate map visualizations and Region map visualizations.
map.regionmap:-
Specifies additional vector layers for use in Region Map visualizations. Supported on Elastic Cloud Enterprise. Each layer object points to an external vector file that contains a geojson FeatureCollection. The file must use the WGS84 coordinate reference system and only include polygons. If the file is hosted on a separate domain from Kibana, the server needs to be CORS-enabled so Kibana can download the file. The following example shows a valid regionmap configuration.
map.regionmap: includeElasticMapsService: false layers: - name: "Departments of France" url: "http://my.cors.enabled.server.org/france_departements.geojson" attribution: "INRAP" fields: - name: "department" description: "Full department name" - name: "INSEE" description: "INSEE numeric identifier" map.regionmap.includeElasticMapsService:- Turns on or off whether layers from the Elastic Maps Service should be included in the vector layer option list. Supported on Elastic Cloud Enterprise. By turning this off, only the layers that are configured here will be included. The default is
true. map.regionmap.layers[].attribution:- Optional. References the originating source of the geojson file. Supported on Elastic Cloud Enterprise.
map.regionmap.layers[].fields[]:- Mandatory. Each layer can contain multiple fields to indicate what properties from the geojson features you wish to expose. The example above shows how to define multiple properties. Supported on Elastic Cloud Enterprise.
map.regionmap.layers[].fields[].description:- Mandatory. The human readable text that is shown under the Options tab when building the Region Map visualization. Supported on Elastic Cloud Enterprise.
map.regionmap.layers[].fields[].name:- Mandatory. This value is used to do an inner-join between the document stored in Elasticsearch and the geojson file. For example, if the field in the geojson is called
Locationand has city names, there must be a field in Elasticsearch that holds the same values that Kibana can then use to lookup for the geoshape data. Supported on Elastic Cloud Enterprise. map.regionmap.layers[].name:- Mandatory. A description of the map being provided. Supported on Elastic Cloud Enterprise.
map.regionmap.layers[].url:- Mandatory. The location of the geojson file as provided by a webserver. Supported on Elastic Cloud Enterprise.
map.tilemap.options.attribution:- Default:
"© [Elastic Maps Service]https://www.elastic.co/elastic-maps-service"The map attribution string. Supported on Elastic Cloud Enterprise. map.tilemap.options.maxZoom:- Default: 10 The maximum zoom level. Supported on Elastic Cloud Enterprise.
map.tilemap.options.minZoom:- Default: 1 The minimum zoom level. Supported on Elastic Cloud Enterprise.
map.tilemap.options.subdomains:- An array of subdomains used by the tile service. Specify the position of the subdomain the URL with the token
{s}. Supported on Elastic Cloud Enterprise. map.tilemap.url:- The URL to the tileservice that Kibana uses to display map tiles in tilemap visualizations. Supported on Elastic Cloud Enterprise. By default, Kibana reads this url from an external metadata service, but users can still override this parameter to use their own Tile Map Service. For example:
"https://tiles.elastic.co/v2/default/{z}/{x}/{y}.png?elastic_tile_service_tos=agree&my_app_name=kibana" ops.interval:- Default: 5000 Set the interval in milliseconds to sample system and process performance metrics. The minimum value is 100.
path.data:- Default:
dataThe path where Kibana stores persistent data not saved in Elasticsearch. pid.file:- Specifies the path where Kibana creates the process ID file.
server.basePath:- Enables you to specify a path to mount Kibana at if you are running behind a proxy. Use the
server.rewriteBasePathsetting to tell Kibana if it should remove the basePath from requests it receives, and to prevent a deprecation warning at startup. This setting cannot end in a slash (/). server.cors:- Default:
falseSet totrueto enable CORS support. This setting is required to configureserver.cors.origin. server.cors.origin:- Default: none Specifies origins. “origin” must be an array. To use this setting, you must set
server.corstotrue. To accept all origins, useserver.cors.origin: ["*"]. server.customResponseHeaders:- Default:
{}Header names and values to send on all responses to the client from the Kibana server. server.defaultRoute:- Default: “/app/kibana” This setting specifies the default route when opening Kibana. You can use this setting to modify the landing page when opening Kibana. Supported on Elastic Cloud Enterprise.
server.host:- Default: “localhost” This setting specifies the host of the back end server.
server.keepaliveTimeout:- Default: “120000” The number of milliseconds to wait for additional data before restarting the
server.socketTimeoutcounter. server.maxPayloadBytes:- Default: 1048576 The maximum payload size in bytes for incoming server requests.
server.name:- Default: “your-hostname” A human-readable display name that identifies this Kibana instance.
server.port:- Default: 5601 Kibana is served by a back end server. This setting specifies the port to use.
server.rewriteBasePath:- Default: false Deprecated setting that specifies if Kibana should rewrite requests that are prefixed with
server.basePath, or require that they are rewritten by your reverse proxy. server.socketTimeout:- Default: “120000” The number of milliseconds to wait before closing an inactive socket.
server.ssl.certificate:andserver.ssl.key:- Paths to the PEM-format SSL certificate and SSL key files, respectively.
server.ssl.certificateAuthorities:- List of paths to PEM encoded certificate files that should be trusted.
server.ssl.cipherSuites:- Default: ECDHE-RSA-AES128-GCM-SHA256, ECDHE-ECDSA-AES128-GCM-SHA256, ECDHE-RSA-AES256-GCM-SHA384, ECDHE-ECDSA-AES256-GCM-SHA384, DHE-RSA-AES128-GCM-SHA256, ECDHE-RSA-AES128-SHA256, DHE-RSA-AES128-SHA256, ECDHE-RSA-AES256-SHA384, DHE-RSA-AES256-SHA384, ECDHE-RSA-AES256-SHA256, DHE-RSA-AES256-SHA256, HIGH,!aNULL, !eNULL, !EXPORT, !DES, !RC4, !MD5, !PSK, !SRP, !CAMELLIA. Details on the format, and the valid options, are available via the OpenSSL cipher list format documentation.
server.ssl.clientAuthentication:- Default: none Controls the server’s behavior in regard to requesting a certificate from client connections. Valid values are
required,optional, andnone.requiredforces a client to present a certificate, whileoptionalrequests a client certificate but the client is not required to present one. server.ssl.enabled:- Default: “false” Enables SSL for outgoing requests from the Kibana server to the browser. When set to
true,server.ssl.certificateandserver.ssl.keyare required. server.ssl.keyPassphrase:- The passphrase that will be used to decrypt the private key. This value is optional as the key may not be encrypted.
server.ssl.redirectHttpFromPort:- Kibana will bind to this port and redirect all http requests to https over the port configured as
server.port. server.ssl.supportedProtocols:- Default: TLSv1.1, TLSv1.2 An array of supported protocols with versions. Valid protocols:
TLSv1,TLSv1.1,TLSv1.2 status.allowAnonymous:- Default: false If authentication is enabled, setting this to
trueenables unauthenticated users to access the Kibana server status API and status page. vega.enableExternalUrls:- Default: false Set this value to true to allow Vega to use any URL to access external data sources and images. If false, Vega can only get data from Elasticsearch.
xpack.license_management.enabled- Default: true Set this value to false to disable the License Management user interface.
xpack.rollup.enabled:- Default: true Set this value to false to disable the Rollup user interface.
i18n.locale- Default: en Set this value to change the Kibana interface language. Valid locales are:
en,zh-CN,ja-JP.
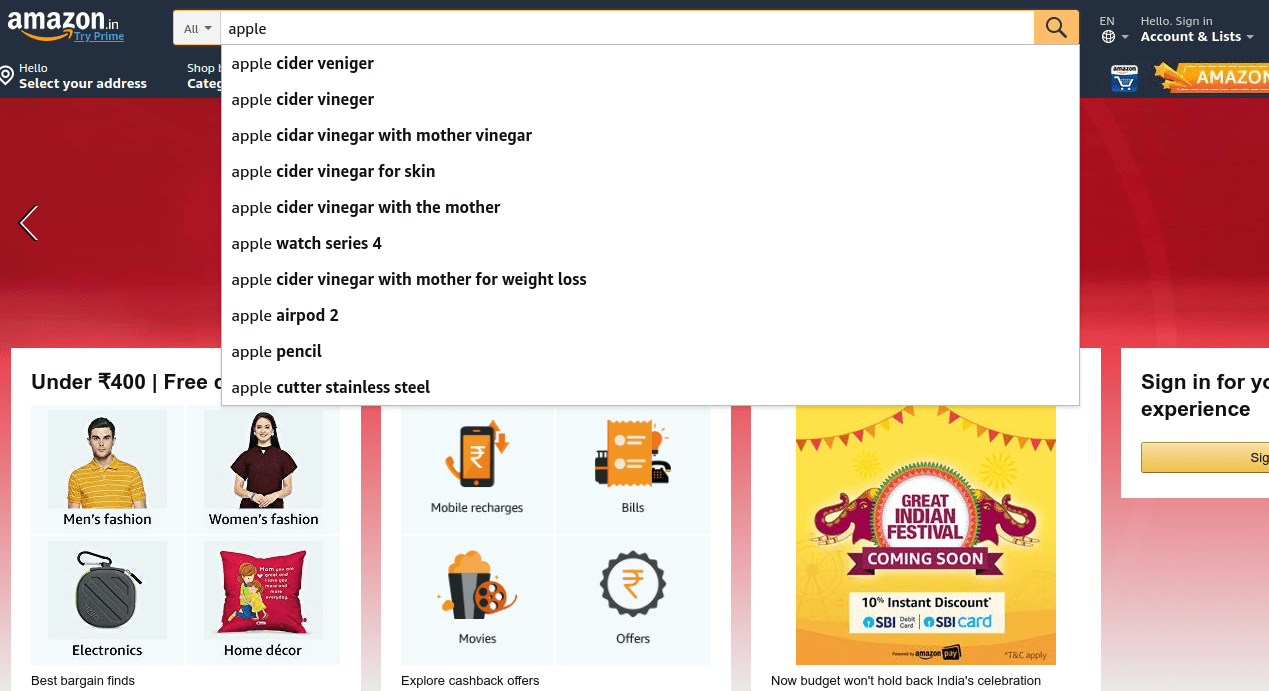
Creating an autocomplete or an auto suggest search bar is often involves a very complicated and elaborate process if you follow the conventional methods and try to build one for yourself. Especially if you are running a small website on WordPress using woocommerce then you will rarely have the time and money to invest in building an autosuggest search bar all by yourself. However you cannot ignore the search functionality and not have a wordpress woocommerce search bar this will do more harm than good.
This is exactly where a woocommerce smart search app or sometimes called as a woocommerce product search box widget really shines. These search plugins offer all the benefits of having a great search bar without having the need to ever invest a lot of time and energy on building it. The other functionality that goes hand in hand with the search plugin is the woocommerce filter plugin. This is a also pretty resource centric to setup if tried to be done all by yourself. It is best advisable to get a woocommerce search and filter plugin. Having a product filter for woocommerce is a also a primary requirement these days and there is absolutely no substitute for it. Product filters can also be facets at times and these names are used interchangeably most of the times even though there is a light difference when it comes to the actual meaning, however getting a faceted search woocommerce app will do the same functionality as getting a woocommerce product search filter plugin. ultimately having a filter or a facet option is a necessary feature that has to be included in the site. Therfore getting a faceted search woocommerce product filter solution is a must for the site.