WordPress administrators beware! A recent discovery of critical vulnerabilities in the popular Automatic plugin (premium version) has put thousands of websites at risk by exposing the websites to a potential takeover. The WP Automatic plugin is estimated to have over 40,000 active installations, making it a prime target for attackers, this plugin allows users to automatically import content from various sources. It gathers content of all formats (e.g. text, images, video) from various places like YouTube, Instagram, Twitter, websites, and more, then posts it on your site according to your preferences

Researcher Rafie Muhammad of Patchstack discovered two critical vulnerabilities in the Automatic plugin on March 13, 2024, both of which can be exploited by attackers to gain unauthorized access to your website and wreak havoc, The vulnerabilities are known as CVE-2024-27956 and CVE-2024-27954, These flaws could allow attackers to steal data, inject malware, or even take complete control of your site. Knowing these vulnerabilities is key to fixing them and securing your site. Here’s a closer look at each vulnerability!
The vulnerabilities:
1. Unauthenticated Arbitrary SQL Execution (CVE-2024-27956)
2. Unauthenticated Arbitrary File Download and SSRF (CVE-2024-27954)
1. Unauthenticated Arbitrary SQL Execution (CVE-2024-27956)
- The first vulnerability, CVE-2024-27956, is found in the file named “inc/csv.php” within the WordPress Automatic plugin, with a CVSS score of 9.9 (considered critical), is an unauthenticated SQL injection flaw.
- The inc/csv.php file in the Automatic plugin accepts user input without proper validation in the $q variable. This allows attackers to inject and execute arbitrary SQL code on the website’s database.

- In simpler terms, the plugin accepts user input and stores it in a variable without properly checking it. This allows attackers to inject malicious SQL code that gets executed on the website’s database, potentially causing severe damage. This can lead to them gaining unauthorized access, stealing sensitive data, or even adding new administrator accounts.
2. Unauthenticated Arbitrary File Download and SSRF (CVE-2024-27954)
- The second critical vulnerability, identified as CVE-2024-27954 resides in the “downloader.php file” within the WordPress Automatic plugin, with a CVSS score of 9.3, allows unauthenticated arbitrary file download and Server-Side Request Forgery (SSRF).
- The downloader.php file in the Automatic plugin allows attackers to download arbitrary files or trick the server into external requests through a vulnerable parameter ($_GET[‘link’]).
- This vulnerability allows attackers to download arbitrary files from your website’s server or even execute malicious code on your server. This could potentially allow attackers to launch SSRF attacks, allowing them to execute unauthorized commands on the server, expose sensitive data like login credentials, or install backdoors for long-term access.
The Tactics and Backdoors:
Since the public disclosure of these vulnerabilities in March 2024, security researchers at WPScan have detected over 5.5 million attempted attacks exploiting these flaws. Here’s what attackers are doing to exploit these vulnerabilities and maintain control over the compromised websites
- Creating Administrator Accounts: Attackers are leveraging the SQL injection vulnerability to create new administrator accounts with usernames like “xtw”. These accounts grant them full control over the compromised website.
- Planting Backdoors: Once inside, attackers plant backdoors such as malicious PHP files named “web.php” and “index.php”. These backdoors allow them to maintain access even if the vulnerabilities are patched.
- Obfuscating Code: To evade detection, attackers often obfuscate the code of their backdoors, making them harder to identify and remove.
- Renaming Vulnerable Files: In some cases, attackers rename the vulnerable “csv.php” file to something else, further hindering detection efforts.
- Escalating Privileges: After gaining initial access, attackers may install additional plugins that allow them to upload files or edit code, giving them even more control over the website.
By providing indicators, WPScan offers clues to help website owners figure out if their site has been hacked.
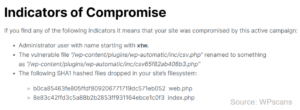
How Does This Affect You?
These vulnerabilities are dangerous because they allow attackers to take complete control of an affected website. They can steal sensitive data, inject malicious code, or even redirect visitors to phishing sites.
What You Should Do?
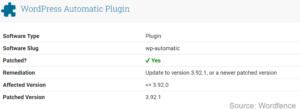
If you use the Automatic plugin on your WordPress website, it’s crucial to update to version 3.92.1 or later immediately. This update patches both the aforementioned vulnerabilities.
To safeguard your website against these vulnerabilities and comparable threats, also contemplate the following measures:
- Maintain Backups: Regularly create backups of your website’s files and database. This allows you to restore your site
- Good Security: Implement strong passwords for all user accounts and security scanners.
- Implement a web application firewall (WAF): For an additional security layer.
- Active updates: keep your WordPress core and plugins updated, Regularly update all plugins and themes to benefit from security patches.
By following these recommendations and staying informed about potential threats, website owners can significantly enhance their security posture and minimize the risk of cyberattacks
The Patch:
Both vulnerabilities have been addressed in version 3.92.1 of the plugin
ValvePress, the plugin’s developer, released updates to address these vulnerabilities:
- CVE-2024-27956 fix: The vulnerable code (inc/csv.php) was entirely removed.
- CVE-2024-27954 fix: New security measures were implemented, including requiring user permissions and unique values only accessible to authorized users.
- Also additionally, validation checks have been added for the URL fetching parameter and downloaded files
While these patches mitigate the immediate risks, it’s crucial to stay vigilant about website security.
In conclusion:
The vulnerabilities in the Automatic plugin serve as a stark reminder of the importance of secure plugin development, especially for tools dealing with database access and URL fetching. Website owners using the Automatic plugin must update to the latest version immediately (3.92.1 or later).
Patchstack recommends imposing strict controls on SQL query execution and URL fetch processes, even for high-privilege users like administrators. Consider using WordPress’s secure functions like wp_safe_remote_* for fetching URLs to enhance security. Choosing plugins with a strong security focus is also crucial for maintaining a secure online presence.
Thus prioritizing regular updates for all plugins and themes and following best security practices, can help protect your website from these and other potential threats.
References:
1. Wpscan- https://wpscan.com/blog/new-malware-campaign-targets-wp-automatic-plugin/
Add great search to your website



