WordPress websites using the Forminator plugin are at risk! Multiple vulnerabilities have been discovered in the plugin, allowing attackers with opportunities to potentially extract sensitive data, manipulate website appearances, or seize complete command over compromised sites. If you use the Forminator plugin to craft engaging forms for your visitors, we have some important information
Japan’s CERT (Computer Emergency Response Team) has alerted users to a vulnerability in the widely-used “Forminator WordPress plugin”, created by WPMU DEV. This warning highlights a critical vulnerability that enables unrestricted file uploads to the server, posing significant risks to over 500,000 installations of the plugin and yours could be one of them.

Due to the recent warning from Japan’s CERT highlighting critical vulnerabilities in the Forminator WordPress plugin, it’s essential for all Forminator users to take immediate action, as this plugin is susceptible to unrestricted file uploads, posing a severe risk to website owners and users. This article details the critical flaws, their potential impact, and the recommended course of action for website administrators.
Forminator and its Vulnerabilities to Be Aware Of:
Forminator is a zero-cost WordPress plugin that allows you to easily customize various forms for your website. It uses a user-friendly drag-and-drop interface, making it accessible even for users without coding knowledge. Its primary function is to enable users to easily create various types of forms, Some of the forms you can create with Forminator include standard contact forms, quizzes, polls, and more.
Japan’s CERT security has discovered and mentioned the following three vulnerabilities in their JVN site.

1. Unrestricted Upload of File with Dangerous Type (CVE-2024-28890):
- Vulnerability score 9.8 out of 10
- This is the most concerning vulnerability identified and is tracked as CVE-2024-28890 as it carries a CVSS score of 9.8, indicating its critical severity. The “Unrestricted upload of file with dangerous type” vulnerability refers to a security flaw in a web application that allows users to upload files to the server without proper validation of file types. This means that malicious users can upload files containing harmful scripts or executable code, such as malware or shell scripts, to the server.
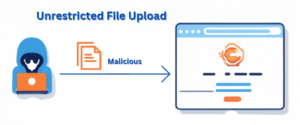
This vulnerability enables remote attackers to directly upload malicious code onto WordPress websites that utilize the Forminator plugin.
Reason for this condition:
- Lack of File Type Validation
- Insufficient Filtering
- Failure to Enforce File Size Limits
- Insecure File Storage
- Lack of Server-side Validation
Impacts:
- Data Theft: Attackers could gain access to sensitive information stored on the website, such as user login credentials, personal details, or financial data.
- Website Defacement: Malicious code could be used to alter the website’s content, displaying misleading information, or disrupt user experience.
- Denial-of-Service (DoS) Attacks: Attackers could exploit the vulnerability to overload the website with traffic, making it inaccessible to legitimate users.
2. SQL Injection (CVE-2024-31077):
- Vulnerability score 7.2 out of 10
- SQL injection is a code injection method that involves injecting malicious SQL code into a web application’s input fields. This code is designed to manipulate the backend database, allowing attackers to retrieve unauthorized information that was not meant to be accessed.
- For example: By exploiting a SQL injection vulnerability present in a login form, an attacker can bypass the authentication process and illicitly access confidential information. This includes sensitive data like user credentials and personal details.

Reason for this condition:
- Lack of Input Validation
- Failure to Use Parameterized Queries
- Outdated or Improper Database Sanitization
Impacts:
- Unauthorized Data Access
- Data Manipulation
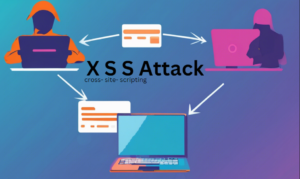
3. Cross-Site Scripting (XSS) (CVE-2024-31857):
- Vulnerability score 6.1 out of 10
- Cross-site scripting (XSS) is an attack method that involves injecting malicious code, typically scripts, into a vulnerable web application. Unlike other attack methods that target the application directly, XSS poses a threat to the application’s users. This results in the compromised page serving harmful code to other visitors, enabling attackers to implant malicious scripts into WordPress sites.
Reason for this condition:
- To know more about XSS vulnerability check out this article
Impacts:
- Malicious Redirection
- session cookies theft
- Control over the affected site
Patch Now to stay safe:
The good news is that patches for these vulnerabilities have been released by WPMU DEV, the developers behind Forminator. Website administrators using the plugin are strongly urged to update to the latest version (1.29.3) as soon as possible. A security patch refers to an update that nullifies specific vulnerabilities, usually released by the developers.
The developers of Forminator (WPMU DEV) have addressed this issue by releasing a comprehensive security patch “Forminator (version:1.29.3)”.This update addresses all three security vulnerabilities in the plugin – Restricted file upload, SQL Injection, and XSS attacks which makes them susceptible to various malicious activities, including data theft, website alteration, and distributed denial-of-service (DDoS) attacks.
For the users of Forminator Secure Your Site with the Latest Update :
Update Forminator to version 1.29.3 as soon as possible. This update patches all the vulnerabilities and keeps your website safe from potential attacks.
Why is this important?
By updating, you’re protecting your website from attackers who could steal information, mess with your content, or even shut it down completely. Taking this quick and simple action guarantees the security of your website and the data of your visitors. If you’re not comfortable updating plugins yourself, consider managed WordPress hosting services. They can handle updates and other security measures for you.
Conclusion:
In conclusion, With the recent warning from Japan’s CERT highlighting critical vulnerabilities in the Forminator WordPress plugin, it’s essential for all Forminator users to take immediate action. Given the magnitude of potential harm that can be caused by these vulnerabilities, it is crucial for all Forminator users to update their installations to the latest patched version.
This proactive measure will significantly reduce the risk of sensitive information exposure, site alteration, and other malicious activities that could severely impact their websites and potentially compromise user data. With a significant number of sites still running vulnerable versions of Forminator, the risk of cyber attacks is alarmingly high. Don’t wait until it’s too late. Take control of your website’s security by updating to Forminator version 1.29.3 immediately, Remember, proactive measures today can prevent the repercussions of a cyber attack tomorrow.
Reference:
Japan’s CERT Portal JVN- https://jvn.jp/en/jp/JVN50132400/