If ensuring thorough checks for vulnerabilities and security measures is a top priority for you, then the recent developments regarding the Essential Addons for Elementor plugin demand immediate attention.
Wordfence security researchers have detected a vulnerability in the popular, extensively used Essential Addons for Elementor plugin. This may potentially endanger numerous WordPress websites (approx 2+ million) associated with them. This vulnerability is identified as Stored Cross-Site Scripting (XSS), which poses a significant risk to site security.
Who does this vulnerability affect?
This vulnerability primarily affects the users of the Essential Addons for Elementor plugin, particularly those who rely heavily on its features and functionalities for their WordPress websites. Essential Addons for Elementor enhances the capabilities of the widely-used Elementor page builder, providing additional options for customizing websites. This add-on provides users with even more features and widgets to customize their websites.
who is least affected:
- Users who don’t use Essential Addons for Elementor: Are not vulnerable to this specific flaw.
- Users who have updated to version 5.9.13: Their websites are protected against the XSS vulnerability addressed.
Cross-Site Scripting (XSS) attack:
Cross-site scripting (XSS) denotes an attack technique that inserts harmful code usually scripts into a weak web application. Unlike other web attack techniques, XSS doesn’t directly aim at the application itself; rather, it puts the application’s users at risk. There are different types of Cross-site Scripting vulnerability; The vulnerability discovered in Essential Addons for Elementor is of a type XSS attack called “Stored (persistent) Cross-Site Scripting (XSS)”, here the bad code inserted by the attacker on the website is stored on the server, like in a database. This causes the website to give out harmful code to other visitors when they come to the affected page, Thus allowing attackers to sneak malicious codes (scripts) into the WordPress sites.
“The Countdown Widget” and “The Woo Product Carousel Widget” are the two particular widgets that are part of the Essential Addons for Elementor plugin where this vulnerability resides. The researchers point to both, a lack of proper input sanitization and output escaping as contributing factors to this vulnerability. Input sanitization – it involves examining and filtering input data to ensure it lacks any characters or strings capable of injecting malicious code into an application or system, thereby enhancing security. Output escaping – it is a method used to eliminate undesirable data from the output data to safeguard it before it is presented to the end user. Failure to properly sanitize inputs and escape output can leave fields vulnerable to malicious script injections, resulting in the theft of session cookies and subsequent control over the affected site.
Security Patch:
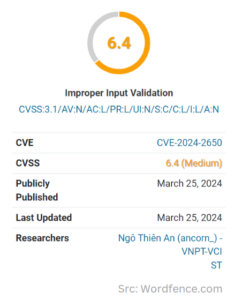
According to Wordfence, this vulnerability requires the attacker to possess ‘contributor-level access’ or higher on the website, thus labeled as an “Authenticated Attacker” as they need some level of access to the website. The vulnerability has a score of 6.4 on a scale of 1 to 10, where 10 is the most critical, making it a “Medium-Level threat”.
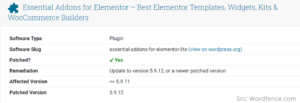
A security patch refers to a specific update released by the developers. The developers of Essential Addons for Elementor have responded to the identified vulnerability by issuing a comprehensive security patch “Essential Addon (version: 5.9.13)”.This update addresses the security vulnerability in the plugin known as Stored Cross-Site Scripting (XSS). This patch primarily addresses the XSS vulnerabilities found in two widgets of the Essential Addons for Elementor plugin: Countdown Widget and Woo Product Carousel Widget. It not only prevents the XSS attack but also fixes other bugs and improves the overall stability and performance of the plugin.
How Can Your Website Be Protected?
To maintain the security of your website, it’s advised to update the Essential Addons for Elementor plugin to version 5.9.13 or later, the newest version (5.9.14) to address this vulnerability. This update fixes the security issue and protects your website against potential XSS attacks.
Conclusion:
For the users of Essential Addons for Elementor, it’s crucial to promptly upgrade to safeguard website integrity.so, upgrade to the most recent version (now at 5.9.14) to mitigate the threat of XSS attacks. This fixes the security issue that could leave your website vulnerable to attacks and bugs.
References:
2.https://wordpress.org/plugins/essential-addons-for-elementor-lite/#developers